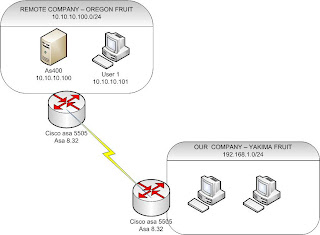
1. You are the new admin of the YAKIMA Company. You decide to filter traffic coming from Oregon to your company. All you want is to allow your users to access only the AS400 server in Oregon.
2. Easy job! You said to yourself. You called the Oregon admin to change the interesting traffic from (10.10.10.0—192.168.1.0) to (10.10.10.100-192.168.1.0) on his side and you are going to do the same from (192.168.1.0 – 10.10.10.0) to (192.168.1.0 – 10.10.10.100).
3. Bummer!!!! The Oregon admin refused saying I don’t want touch that cisco thing. I am not a cisco guy and our cisco consultant is way too expensive. I am sorry I can’t let you touch our device. SO, you are stuck.
4. And then you find me online – another fellow who went to the same dilemma.
5. The solution : VPN filtering using ASDM 6.3 ASA 8.3.4
5.1 Go to Configuration, site-to-site vpn, group policy, click add and internal group policy
Pic1

5.2 Give your policy a name, Uncheck inherit on tunnel protocol and ipv4 filter.
Pc2

Pc2

5.3 click manage and extended ACL, click add ACL, give it a name and then click add ACE – please be careful with the source and destination address – pc3

5.4 click ok twice and you should be back to the internal group policy- click ok - pic4

5.5 Now go to Advanced Tunnel groups, select the correct tunnel , click edit – in the group policy select your new filter policy.pic5
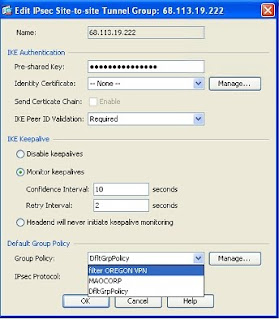
5.6 Click ok and apply –
5.7 It will seems like nothing is working – Now you need to log out the tunnel and ping the server and see the difference
Go to monitoring, vpn, session and choose site-to-site, choose the correct tunnel and click logout.
Pc6

Voila test it and let me know the result.

5.4 click ok twice and you should be back to the internal group policy- click ok - pic4

5.5 Now go to Advanced Tunnel groups, select the correct tunnel , click edit – in the group policy select your new filter policy.pic5

5.6 Click ok and apply –
5.7 It will seems like nothing is working – Now you need to log out the tunnel and ping the server and see the difference
Go to monitoring, vpn, session and choose site-to-site, choose the correct tunnel and click logout.
Pc6

Voila test it and let me know the result.

No comments:
Post a Comment