I am very glad to have this ip power 9258. This is Network based power controller - I am able to power on and off all my cisco routers and switches from anywhere in the world. Because this simple unit, I am saving on electricity and cut off my phone calls to my wife and daughter . I used to call them to turn on devices when I am at starbucks studying.
But there is something I discovered with this ip power that very SCARY. It mapped my ip address to a public ip service server located 122.116.138.126 - Anybody in the world could access my network and turn on and off all my devices. Can you imagine if I plug my production servers into this device?
http://122.116.138.129/test/ip_search.asp
I found lot of ip addresses (ip power devices) with default username and password. I could turn off and on if I wanted to scare people specialy on this halloween days.
SO - PLEASE MAKE SURE YOU CHANGED THE PASSWORD AND DENY ANY TRAFFIC TO 122.116.138.129
You can put it to the test. Change the name of your IP 9258 and go to the website and enter the new hostname. You will be scared.
Thursday, October 28, 2010
Thursday, October 14, 2010
VPN filtering using ASDM 6.3 with ASA 8.3
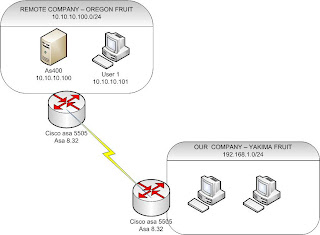
1. You are the new admin of the YAKIMA Company. You decide to filter traffic coming from Oregon to your company. All you want is to allow your users to access only the AS400 server in Oregon.
2. Easy job! You said to yourself. You called the Oregon admin to change the interesting traffic from (10.10.10.0—192.168.1.0) to (10.10.10.100-192.168.1.0) on his side and you are going to do the same from (192.168.1.0 – 10.10.10.0) to (192.168.1.0 – 10.10.10.100).
3. Bummer!!!! The Oregon admin refused saying I don’t want touch that cisco thing. I am not a cisco guy and our cisco consultant is way too expensive. I am sorry I can’t let you touch our device. SO, you are stuck.
4. And then you find me online – another fellow who went to the same dilemma.
5. The solution : VPN filtering using ASDM 6.3 ASA 8.3.4
5.1 Go to Configuration, site-to-site vpn, group policy, click add and internal group policy
Pic1

5.2 Give your policy a name, Uncheck inherit on tunnel protocol and ipv4 filter.
Pc2

Pc2

5.3 click manage and extended ACL, click add ACL, give it a name and then click add ACE – please be careful with the source and destination address – pc3

5.4 click ok twice and you should be back to the internal group policy- click ok - pic4

5.5 Now go to Advanced Tunnel groups, select the correct tunnel , click edit – in the group policy select your new filter policy.pic5
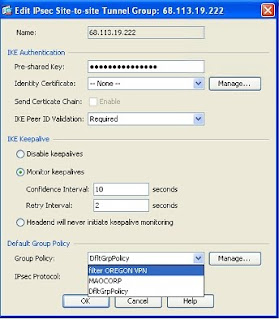
5.6 Click ok and apply –
5.7 It will seems like nothing is working – Now you need to log out the tunnel and ping the server and see the difference
Go to monitoring, vpn, session and choose site-to-site, choose the correct tunnel and click logout.
Pc6

Voila test it and let me know the result.

5.4 click ok twice and you should be back to the internal group policy- click ok - pic4

5.5 Now go to Advanced Tunnel groups, select the correct tunnel , click edit – in the group policy select your new filter policy.pic5

5.6 Click ok and apply –
5.7 It will seems like nothing is working – Now you need to log out the tunnel and ping the server and see the difference
Go to monitoring, vpn, session and choose site-to-site, choose the correct tunnel and click logout.
Pc6

Voila test it and let me know the result.
Thursday, September 30, 2010
SHOW eigrp hello time
It is very simple to know the exact eigrp hello interval on an interface.
The command is :
show ip eigrp (AS) interface detail (interface type)
R2#sh ip eigrp 1 int detail fa0/0.23
IP-EIGRP interfaces for process 1
Xmit Queue Mean Pacing Time Multicast Pending
Interface Peers Un/Reliable SRTT Un/Reliable Flow Timer Routes
Fa0/0.23 1 0/0 4 0/1 50 0
Hello interval is 5 sec
Next xmit serial
Un/reliable mcasts: 0/3 Un/reliable ucasts: 4/4
Mcast exceptions: 1 CR packets: 1 ACKs suppressed: 0
Retransmissions sent: 1 Out-of-sequence rcvd: 0
Authentication mode is not set
Use multicast
R2#
The command is :
show ip eigrp (AS) interface detail (interface type)
R2#sh ip eigrp 1 int detail fa0/0.23
IP-EIGRP interfaces for process 1
Xmit Queue Mean Pacing Time Multicast Pending
Interface Peers Un/Reliable SRTT Un/Reliable Flow Timer Routes
Fa0/0.23 1 0/0 4 0/1 50 0
Hello interval is 5 sec
Next xmit serial
Un/reliable mcasts: 0/3 Un/reliable ucasts: 4/4
Mcast exceptions: 1 CR packets: 1 ACKs suppressed: 0
Retransmissions sent: 1 Out-of-sequence rcvd: 0
Authentication mode is not set
Use multicast
R2#
Sunday, September 12, 2010
quick review of How to enable ssh with a cisco router
here are the steps you need to follow to enable ssh
in config mode
1- hostname ...
2- ip domain-lookup
3- username .... password
4- crypto key-generate rsa
5- ip ssh authentication-retries
6 - ip ssh version
7- line vty 0 4
login local
transport input none
transport input ssh
8 - save your work.
Example from my router:
conf t
Enter configuration commands, one per line. End with CNTL/Z.
R3(config)#hostname SSHSERVER
SSHSERVER(config)#ip domain-name CCIE
SSHSERVER(config)#username BERTRAND password r3
SSHSERVER(config)#crypto key generate rsa
% You already have RSA keys defined named SSHSERVER.CCIE.
% Do you really want to replace them? [yes/no]: y
Choose the size of the key modulus in the range of 360 to 2048 for your
General Purpose Keys. Choosing a key modulus greater than 512 may take
a few minutes.
How many bits in the modulus [512]:
Mar 1 01:31:52.676: %SSH-5-DISABLED: SSH 2.0 has been disabled
1024
% Generating 1024 bit RSA keys, keys will be non-exportable...[OK]
Mar 1 01:32:12.172: %SSH-5-ENABLED: SSH 2.0 has been enabled
SSHSERVER(config)#
SSHSERVER(config)#ip ssh version 2
SSHSERVER(config)#ip ssh authentication-retries 3
SSHSERVER(config)#line vty 0 4
SSHSERVER(config-line)#login local
SSHSERVER(config-line)#transport input none
SSHSERVER(config-line)#transport input ssh
SSHSERVER(config-line)#^Z
SSHSERVER#wr
Building configuration...
access_server#7
% 7 is not an open connection
access_server#6
[Resuming connection 6 to sw1 ... ]
SW1#ssh -l BERTRAND 172.16.50.1 3
Password:
Password:
SSHSERVER>sh ssh
Connection Version Mode Encryption Hmac State Username
66 1.99 IN aes128-cbc hmac-sha1 Session started BERTRAND
66 1.99 OUT aes128-cbc hmac-sha1 Session started BERTRAND
%No SSHv1 server connections running.
SSHSERVER>exit
[Connection to 172.16.50.3 closed by foreign host]
SW1#
in config mode
1- hostname ...
2- ip domain-lookup
3- username .... password
4- crypto key-generate rsa
5- ip ssh authentication-retries
6 - ip ssh version
7- line vty 0 4
login local
transport input none
transport input ssh
8 - save your work.
Example from my router:
conf t
Enter configuration commands, one per line. End with CNTL/Z.
R3(config)#hostname SSHSERVER
SSHSERVER(config)#ip domain-name CCIE
SSHSERVER(config)#username BERTRAND password r3
SSHSERVER(config)#crypto key generate rsa
% You already have RSA keys defined named SSHSERVER.CCIE.
% Do you really want to replace them? [yes/no]: y
Choose the size of the key modulus in the range of 360 to 2048 for your
General Purpose Keys. Choosing a key modulus greater than 512 may take
a few minutes.
How many bits in the modulus [512]:
Mar 1 01:31:52.676: %SSH-5-DISABLED: SSH 2.0 has been disabled
1024
% Generating 1024 bit RSA keys, keys will be non-exportable...[OK]
Mar 1 01:32:12.172: %SSH-5-ENABLED: SSH 2.0 has been enabled
SSHSERVER(config)#
SSHSERVER(config)#ip ssh version 2
SSHSERVER(config)#ip ssh authentication-retries 3
SSHSERVER(config)#line vty 0 4
SSHSERVER(config-line)#login local
SSHSERVER(config-line)#transport input none
SSHSERVER(config-line)#transport input ssh
SSHSERVER(config-line)#^Z
SSHSERVER#wr
Building configuration...
access_server#7
% 7 is not an open connection
access_server#6
[Resuming connection 6 to sw1 ... ]
SW1#ssh -l BERTRAND 172.16.50.1 3
Password:
Password:
SSHSERVER>sh ssh
Connection Version Mode Encryption Hmac State Username
66 1.99 IN aes128-cbc hmac-sha1 Session started BERTRAND
66 1.99 OUT aes128-cbc hmac-sha1 Session started BERTRAND
%No SSHv1 server connections running.
SSHSERVER>exit
[Connection to 172.16.50.3 closed by foreign host]
SW1#
Saturday, September 4, 2010
RemoteApp disconnected - The client could not connect - Remote desktop
I installed RemoteApp from Terminal Server and Distribute the application to all users. But one of the users who work from home (Remote worker - Location: idaho) is experiencing some weird problem.
When he clicked on the Famous software (remote Apps), he receive the message
"The client could not connect. You are already connected to the console of this computer. A new console session cannot be established".
After 30 minutes of troubleshooting, I discovered the cause of the problem and I wanted to share the solution with my audience.
The problem was that the user home network subnet is 192.168.1.0/24 same as my office network and worse his computer has the same ip address as my terminal server 192.168.1.2 -
so when the vpn to our network, the remoteApps is confuse about the exact location of the terminal server because the 192.168.1.2 is belong the host iniated the connection.
To fix the problem without causing too much pain to my users, I changed the user computer IP adddress from 192.168.1.2 to 192.168.1.55 (a ramdom number) and voila the remoteApps work and the client was able to access famous software (it is our accounting software).
But the best way to fix this problem and the one I will recommend is to change the subnet address of the user home network. For example, give it the subnet address of 10.10.10.0/24 if not used in your organization.
Thanks
Wednesday, August 25, 2010
Famous Software - Unable to print tag label
When click save or F12 nothing happens on the screen or the printer label.
Solution: Give full permission to everyone to the following folders:
1- The famous server itself, give full permission to everyone to : c:\famous client
2- In the terminal server give full permission to everyone to c:\famous client
Solution: Give full permission to everyone to the following folders:
1- The famous server itself, give full permission to everyone to : c:\famous client
2- In the terminal server give full permission to everyone to c:\famous client
Famous software - print error 2
Today, the repacking station was acting weird. Tom called me and said that when he click on save (or F12) on famous to print a tag, he receive printer error 2.
Here how I fixed the problem:
Cause: The printer name in the famous propriety is different from the name in the terminal server.
Solution:
1- Go the terminal server and check the name of the printer,
2- On the station, launch famous, click file, proprieties
3- Choose the correct printer name.
Here how I fixed the problem:
Cause: The printer name in the famous propriety is different from the name in the terminal server.
Solution:
1- Go the terminal server and check the name of the printer,
2- On the station, launch famous, click file, proprieties
3- Choose the correct printer name.
Sunday, May 16, 2010
How to connect securely to your home lab
I don't know if I have share this you. But I have a home lab that I connect to from virtually anywhere in the world.
My home lab as an access server cisco 2509. As you surely know, the cisco access server 2509 doesn't support ssh connection and you know how insecure it is to use telnet.
To securely connect to my access server and freely move between my 10 others routers, I setup a remote vpn on my asa 5505.
So, now each time, I want to connect to my home lab to practice, I launch first my cisco vpn client, connect and then telnet to access server located at 10.2.1.3
I will post a video about my configuration step by step.
By the way, I don't have a static IP since my ISP CHARTER COMM can't give me one unless I sign up for the business account which will cost me more than $50.00 than what I am paying right now.
My home lab as an access server cisco 2509. As you surely know, the cisco access server 2509 doesn't support ssh connection and you know how insecure it is to use telnet.
To securely connect to my access server and freely move between my 10 others routers, I setup a remote vpn on my asa 5505.
So, now each time, I want to connect to my home lab to practice, I launch first my cisco vpn client, connect and then telnet to access server located at 10.2.1.3
I will post a video about my configuration step by step.
By the way, I don't have a static IP since my ISP CHARTER COMM can't give me one unless I sign up for the business account which will cost me more than $50.00 than what I am paying right now.
Friday, May 14, 2010
New blog
i am sorry I did not post in this blog since dec 2009.
I started a new blog with google apps and I hope I will be able to link these 2 blogs.
The new blog is http://www.tititec.com
I started a new blog with google apps and I hope I will be able to link these 2 blogs.
The new blog is http://www.tititec.com
Subscribe to:
Comments (Atom)
